We describe in 5 steps how to protect your business against DDoS attacks of any size.
Welcome , today is Tuesday, April 16, 2024
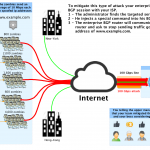 How to Protect Successfully your network against DDoS attacks: 5 steps
How to Protect Successfully your network against DDoS attacks: 5 stepsWe describe in 5 steps how to protect your business against DDoS attacks of any size.