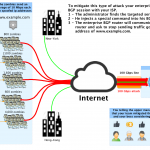
Every businesses need DDoS protection.
Today it’s important for the success of your business to have an online presence. You always thought that you would never be a victim of DDoS attacks. But, what would happen if your website or online application is down because of a DDoS attack?
Here are some facts taken from digitalattackmap:
- Attacks are cheaper (150$ for a week long DDoS)
- Their number are increasing every weeks (2000/day)
- Increase attributed downtime (1/3 of all downtime incidents)
You can even block a 1TB DDoS attack!
With enough preparation, anybody can block a DDoS attack of any size and we will tell you how in 5 steps.
- Become invisible
- Filter aggressively
- Identify attack patterns
- Block traffic patterns
- Deploy counter-measures solutions
1. Become invisible
The attackers will constantly probe your network through many techniques to measure the availability of your online services. Ping is a command commonly use to measure the round trip time to reach a server on internet.
Output of the ping command under normal conditions.
ping www.example.com PING na01.mycdn.example.com (xx.yyy.208.170): 56 data bytes 64 bytes from xx.yyy.208.170: icmp_seq=0 ttl=58 time=39.296 ms 64 bytes from xx.yyy.208.170: icmp_seq=1 ttl=58 time=39.163 ms 64 bytes from xx.yyy.208.170: icmp_seq=2 ttl=58 time=41.742 ms 64 bytes from xx.yyy.208.170: icmp_seq=3 ttl=58 time=40.187 ms
Output of the ping command under DDoS attacks.
ping www.example.com PING na01.mycdn.example.com (xx.yyy.208.170): 56 data bytes 64 bytes from xx.yyy.208.170: icmp_seq=0 ttl=58 time=1028.296 ms 64 bytes from xx.yyy.208.170: icmp_seq=1 ttl=58 time=39.163 ms 64 bytes from xx.yyy.208.170: icmp_seq=2 ttl=58 time=458.742 ms 64 bytes from xx.yyy.208.170: icmp_seq=3 ttl=58 time=765.187 ms
Did you notice that the time in ms is not very regular?
This is exactly what happen when you are under DDoS attack. The time to reach your enterprises services is multiply x25 to finally become unavailable. The attackers also use this information to measure the effectiveness of their attacks.
Output of the ping command when invisible.
ping www.example.com PING na01.mycdn.example.com (xx.yyy.208.170): 56 data bytes Request timeout for icmp_seq 0 Request timeout for icmp_seq 1 Request timeout for icmp_seq 2 Request timeout for icmp_seq 3
It’s important to become invisible early in the game. A simple icmp firewall ruleset well tested and apply on the edge routers can really make the difference during the battle.
2. Filter aggressively
It’s now time to prepare for your next move. In a previous post, we described the steps to do in preparation for a DDoS attack. It’s now time to apply these already prepared steps. You did prepare them, right?
Enable SYNproxy
Enable a black list
Enable aggressive rate-limiting
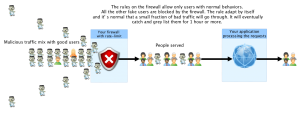
Make sure that your critical applications and infrastructure services don’t receive junk traffic. It’s important to keep a clean flow of network traffic towards your application servers by enabling syn proxy, tight rate-limiting rules and known black lists. These protections will remain active throughout the DDoS attack. They will catch most of the junk traffic automatically for you.
You are now protecting more than your attackers expected in less than 1 minute! The attackers will start noticing they chose the wrong adversary.
This is when the battle starts.
3. Identify attack patterns
In every battle, your enemies will choose different ways to bring your online services down. Now it’s time to identify the strategy used by the attackers. These obscure techniques are well documented and we will explain you which tool to use to identify every attack types.
Read more about DDoS
What is a DDoS attack?
DDoS protection
3.1 Graphs
Gathering information about your consumers is not only useful to your marketing department. It can also be useful to identify potential attack patterns. Tools like ntop and netflow will gather meta data about the traffic patterns. You can then run reports base on source and destination ip addresses to identify the patterns.
Useful to detect volumetric attack
In this example you will find which host in your network is the victim of a volumetric attack. Locate the server receiving an abnormal high amount of Host contacts.
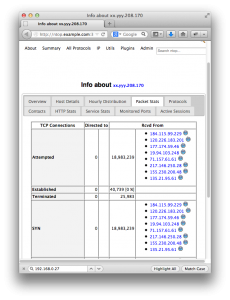
Is it a SYN flood attack?
The number of Attempted connections and SYN are abnormally higher than the number of Established connections.
3.2 Tcpdump
This is a powerful command line tools that display in real time the network traffic information such as source and destination addresses. This tool has the advantage to quickly identify the big canons out there.
Always use the flag -c 100 to limit the amount of packets capture by tcpdump.
Useful to detect DNS amplification
In this example you will hunt which servers are sending you the traffic. This attack happen on the well known udp port 53. Make sure to filter out your own dns server when gathering samples.
tcpdump -nnni bond0 -c 100 -w sample.txt dst port 53 19:36:10.892247 IP 168.61.144.13.16604 > xx.yyy.208.170.domain: 22115+ [1au] ANY? anonsc.com. (39) 19:36:10.904985 IP 168.61.144.13.34834 > xx.yyy.208.170.domain: 34811+ [1au] ANY? anonsc.com. (39) 19:36:10.904994 IP 168.61.144.13.50965 > xx.yyy.208.170.domain: 57326+ [1au] ANY? anonsc.com. (39) 19:36:10.907735 IP 178.18.84.225.36011 > xx.yyy.208.170.domain: 12517+ [1au] ANY? anonsc.com. (39) 19:36:10.914599 IP 178.18.84.225.37095 > xx.yyy.208.170.domain: 60075+ [1au] ANY? anonsc.com. (39) 19:36:10.917676 IP 112.198.79.94.42688 > xx.yyy.208.170.domain: 21263+ [1au] ANY? anonsc.com. (39) ... 19:36:11.023627 IP 71.81.227.222.53296 > xx.yyy.208.170.domain: 62188+ [1au] ANY? anonsc.com. (39) 19:36:11.023648 IP 71.81.227.222.20048 > xx.yyy.208.170.domain: 166+ [1au] ANY? anonsc.com. (39) 19:36:11.199172 IP 168.61.144.13.20559 > xx.yyy.208.170.domain: 17865+ [1au] ANY? anonsc.com. (39) 19:36:11.200294 IP 178.18.84.225.64698 > xx.yyy.208.170.domain: 34045+ [1au] ANY? anonsc.com. (39)
You now see junk traffic that is part of the DDoS attack. How can you easily find out which one are the big cannons? You need to parse, filter and sort this output into a human readable format.
Find out which bogus DNS resolvers are sending you an amplified attack.
awk '{print $3}' sample.txt | cut -d '.' -f1-4 | sort | uniq -c | sort -nr
48 178.18.84.225
44 168.61.144.13
6 71.81.227.222
2 112.198.79.94
This command seems very complicated but, it’s really just parsing, filtering and sorting the output. It’s much easier to see that 178.18.84.225 and 168.61.144.13 are the big canons.
3.3 Network management
Your switches, routers, firewalls and load-balancers are the heart of your online network. You need to know the capacity and limits of all your equipments. You should document how much packets/sec, bandwidth and concurrent connections your infrastructure supports.
You must protect them at all time.
XNA-101#sh int Te0/1 | i rate 30 second input rate 6203155000 bits/sec, 7152679 packets/sec 30 second output rate 167712000 bits/sec, 25887 packets/sec
You should be prepare and know all the troubleshooting commands of your core equipments by heart. It’s not the time to look for help on stackoverflow.
4. Block traffic patterns
With your tools you can now identify attack patterns. You wish they could display an output like this one in real time.
* I like to watch this map.
It’s now time to block the attackers and to have some fun. It’s important to start with the easy patterns that do a lot of damage.
4.1 Layer 4 and application attacks
Identified with: Not applicable
Complexity to stop: easy to medium
Countermeasure: Rate-limit, syn proxy, over-provision
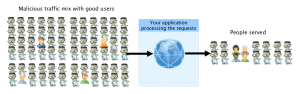
This is the most common attack. The attackers will try to establish as many connections as possible to a common service or application. These services are very sensitive to spikes of connections and are very easy to break. They will target your web, mail, dns, applicaton servers or all of them. You must protect them at all time.
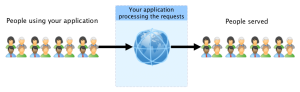
Before an attack
All the users are serve properly because the application can handle the amount of requests.
During an attack
There are more malicious users served than legitimate.
Their goal is to do effective damage quickly by using memory, disk space, or processor time of your servers with fake users.
* Solutions: If you already Filter aggressively you have the proper defense solutions in place. This type of attack will be useless against your network.
4.2 Amplification Attacks
Identified with: tcpdump
Complexity to stop: easy
Countermeasure: Black-hole source
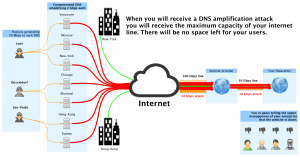
Dns amplification is the flavor of the year 2013. The attackers sends a lot of small ip packets (64 bytes) to a compromise server on internet. They spoof the packets with a source ip address in your network. This compromised server then replies back as fast as possible to the target, you, with 3000 bytes packets. The attacker can generate x45 times more traffic than his actual bandwidth!
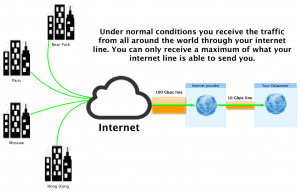
Before an attack
You are receiving less traffic than the maximum limit of your internet line.
During an attack
Their goal is to saturate your internet line by using all the available bandwidth.
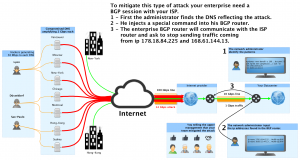
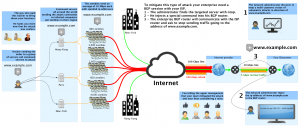
* Solutions: The only way to protect your network against these type of attacks is to black-hole the source ip in your ISP network with BGP. If you run a BGP session with your internet provider you can automatically tell your ISP to ignore this amplified traffic before it’s sent to your network.
4.3 Volumetric Attacks
Identified with: ntop
Complexity to stop: difficult
Solution: over-provision and black-hole destination
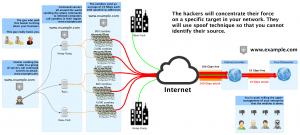
This type of attack is probably the most challenging to stop today. Usually a group of hackers control several thousand of infected computers call zombies. The attackers will send commands to intermediate servers to coordinate attacks toward your network.
During an attack
Their goal is again to isolate your enterprise from internet by using all the available bandwidth.
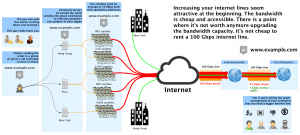
* Solution 1 : The typical solution is to over-provision. Before it was easy to block 100 Mbps DDoS with 1 Gbps internet line. The experts recommend an infrastructure that can support up to 10 times your normal load. But today’s reality is DDoS attacks are of 100 Gbps order.
How to block a 1 TB DDoS attack?
You realized that the zombies are using spoofed ip addresses to send a SYN flood attack. You think the battle is lost because there are millions of spoofed ip addresses attacking you. You then realize that they send 1 TB to 1 destination.
* Solution 2 : We can’t accurately identify the source addresses because they are spoofed, but we know the destination. Black-hole yourself, by telling your isp to stop sending traffic to the attacked target. The zombies will continue to send all the possible Gbps or Tbps to a black-hole. Nothing can escape a black hole, not even light.
Now this service is unreachable because it’s black-holed. It’s time to bring it back online. For this we will use counter-measure solutions.
5. Deploy counter-measures solutions
Congratulations! You stopped the first wave of the DDoS. If you are lucky the DDoS will stop there. If not, they will retry all the possible patterns describe above and probably increase the complexity. It’s now time to deploy counter-measures.
5.1 Sacrifice some ip
What? It sounds weird but yes.
If you receive an attack from a massive DDoS, like the one describe Volumetric Attacks, just black-hole the server they attack. You can then update the DNS entry to another ip address. If you coordinate well, the total downtime notice by your clients will be approximately 5 minutes. What is 5 minutes in a year? Are we still under the five nines?
Another approach is to update the attacked ip address with a DDoS protection provider like cloudflare.
5.2 Deflect amplification attacks
The Amplification Attacks are like an atomic bomb. It can release much more energy than it’s original size and it can easily bring down your business. It’s also very easy to mitigate with BGP because the signature is so easy to recognize.
Write a script that automatically black-hole the source when you receive this specific signature.
5.3 Over-provision
This one is the most interesting for network administrators or the worst nightmare for managers dealing with budgets and monthly recurring charges. It’s easy to say add more servers and add more bandwidth. When you see the bills, you ask yourself if you can optimize your assets.
There is a point where it’s not worth anymore of over over over-provisioning. You need to find how much your enterprise can afford and how big is the risk.
5.4 IPv6
Start implementing IPv6 now. You will need it anyway sooner or later. Try to convince your most important clients to also use an IPv6 platform where DDoS are less likely to happen for now. In the IPv6 world, every enterprise receives at least 18,446,744,073,709,551,616 ip addresses. You can easily sacrifice any ip under a volumetric attack.
Conclusion
We just described you the necessary steps to successfully stop a DDoS of any size. In order to achieve this, you need some preparations, a good infrastructure and BGP. BGP is the key to success in fighting DDoS.
DDoS attacks are continuously evolving and new patterns will appear everyday like the slow attack. You need to stay updated and decipher the patterns of your enemies. If you are constantly a victim of DDoS be sure that there are solutions and experts ready to help you solve this problem.
Are you prepare to face a DDoS? Were you already a victim of DDoS? Share with us what do you think about DDoS.
Jean Debogue
Latest posts by Jean Debogue (see all)
- Phoenix project: Canada first - March 2, 2018
- How to install sieve for dovecot on CentOS 6? - February 8, 2014
- How to Protect Successfully your network against DDoS attacks: 5 steps - November 23, 2013


 How to Protect Successfully your network against DDoS attacks: 5 steps
How to Protect Successfully your network against DDoS attacks: 5 steps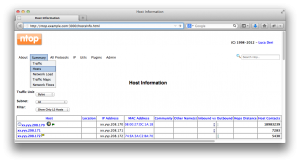
[…] tricks to apply during a DDoS will be explain in another blog. We will also answer the question of how to block the traffic before it’s sent to you in a way that it doesn’t saturate your … Before we explain what to do during an attack it’s important to have a strong defense […]
.
thanks!
maillot football americain
I delight in, end result in I identified just what I was having a appear for. You have ended my 4 day prolonged hunt! God Bless you gentleman. Have a great day. Bye
I really feel like the writer has substantial understanding in this topic. Pretty good put up. I located your site best for my wants. Many thanks for sharing the fantastic suggestions. This is an intriguing and so nicely preserved weblog.
I am delighted that I came upon this blog, I could not learn any info on this subject matter prior to visiting your put up. Thanks God I came across on this weblog and located the pertinent info.
bottes bocage
Extremely very good composed report. It will be supportive to any person who utilizes it, which includes me. Keep doing what you are carrying out a?? cana??r hold out to read a lot more posts.